Government, operators working to update pipeline cybersecurity
Portions of this article were adapted from documents published by the US Government.
On Jan. 29, 2022, Oiltanking GMBH Group and Mabanaft GMBH & Co. KG Group discovered they had been the victim of a cyber incident affecting their information technology (IT) systems, including those underpinning automated tank loading and unloading. The companies secured their systems and are investigating the matter with the help of external specialists, applying contingency plans and seeking to understand the full scope of the incident. All terminals are operating safely.
Oiltanking GMBH Group continued to operate its terminals throughout. Oiltanking Deutschland GMBH & Co. KG (a Mabanaft operating unit) terminals were operating with limited capacity after the incident, and the company declared force majeure. Mabanaft Deutschland GmbH & Co. KG also declared force majeure for most of its inland supply activities in Germany. The outages caused Shell Deutschland GMBH, which has nearly 2,000 German retail outlets, to reroute some of its supplies.
Oiltanking Deutschland’s Terminal Hamburg-Blumensand has 869,805 cu m of liquids storage spread across 72 tanks holding heating oil, diesel, gasoline, and naphtha, among other products. The company has 10 other products terminals in Germany.
Later that same week, a series of so-far-unconnected ransomware attacks affected bulk liquids operations in Belgian and Dutch ports, including those of SEA-invest division SEA-TANK and Evos.
The attacks in northwest Europe were the largest directed at the hydrocarbons industry since May 7, 2021, when malicious actors used DarkSide ransomware and stolen login credentials to conduct a cyberattack against Colonial Pipeline Co.’s business IT network. During the attack, the company disconnected certain industrial control systems, succeeding in preventing them from being compromised. But the disconnection resulted in a temporary halt to operations of the 2.5-million b/d pipeline, leading to gasoline shortages throughout the southeast US.
In 2020, US victims of ransomware attacks paid an estimated $350 million in ransoms, a 311% increase from 2019, with the average payment exceeding $300,000.
And even before then, widespread cyberattacks on infrastructure were occurring. In December 2019, a ransomware attack infected various industrial control systems devices in the US, Europe, and Japan, impairing operation by encrypting files and displaying a ransom note to reinstate them. In 2015 cyberattacks on the Ukrainian power grid opened breakers at the substations of three regional electric utilities, causing a loss of power to about 225,000 customers.
Background
Cybercriminals increasingly target critical infrastructure using ransomware to get money by exploiting cybersecurity gaps. The 2021 Annual Threat Assessment of the US Intelligence Community and the 2020 Homeland Threat Assessment noted that certain nations (China, Russia, Iran, and North Korea) and criminal groups pose the greatest cyberattack threats to US critical infrastructure.
Even a minor pipeline disruption can increase commodity prices, while prolonged disruptions could lead to widespread energy shortages. Protecting US pipelines is the joint responsibility of their operators and the Transportation Security Administration (TSA). TSA, within the Department of Homeland Security (DHS), has primary oversight responsibility for the physical security and cybersecurity of transmission and distribution pipeline systems.
Since 2010, the Government Accountability Office (GAO) has made nearly 80 recommendations for various federal agencies to enhance infrastructure cybersecurity. However, as of December 2020, most of these recommendations (nearly 50) had not been implemented, according to GAO. As a result, the risks of unprotected infrastructures being harmed were heightened.
TSA’s Pipeline Security Branch (PSB) first issued voluntary pipeline security guidelines in 2011 and released revised guidelines in March 2018 and April 2021. The advisories directed critical infrastructure owner-operators to adopt specific mitigation strategies, such as implementing multifactor authentication for remote access to networks; investigating unauthorized connections; and addressing known vulnerabilities by applying software patches or adopting other controls.
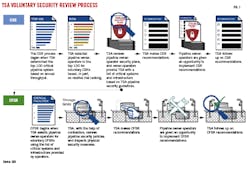
TSA also conducted security reviews of privately owned and operated pipelines. These reviews—Corporate Security Reviews (CSR) and Critical Facility Security Reviews (CFSR) assess the extent to which the 100 most critical pipeline systems are following the intent of TSA’s pipeline security guidelines (see accompanying figure).
TSA issued its first security directive in May 2021 following the Colonial attack.
GAO reports in 2018 and 2019 identified some weaknesses in the agency’s oversight and guidance and made 15 recommendations to address these weaknesses. GAO also reported that TSA had not reviewed or revised its 2010 Pipeline Security and Incident Recovery Protocol Plan to ensure it addressed changes in at least three key areas: cybersecurity-related laws and policies, federal incident management policies for pipeline stakeholders, and DHS’s terrorism alert system.
TSA concurred with GAO’s recommendations and has since addressed most of them, including clarifying portions of its Pipeline Security Guidelines addressing monitoring of security review performance and assessing staffing needs. TSA completed a review of the plan and determined that updates are needed and will require coordination with other agencies.
As of July 2021, however, TSA had not fully addressed two pipeline cybersecurity-related weaknesses identified by GAO:
- Incomplete information for pipeline risk assessments.
- Aged protocols for responding to pipeline security incidents.
TSA had not yet fully identified or developed data sources relevant to threat, vulnerability, and consequence, and incorporated that data into its pipeline relative-risk ranking tool. This could include data on cybersecurity threats, prior attacks, natural hazards, physical pipeline condition, and cross-sector interdependencies. TSA also had not yet conducted a peer review of its risk ranking tool, as GAO had recommended. TSA stated that doing so was contingent on first enhancing the tool. Developing this information and incorporating it into the risk-ranking tool would provide more assurance PSB ranks relative risk among pipeline systems using comprehensive and accurate data.
TSA officials told GAO that a timely update to address current cyber threats is appropriate and that it anticipated updating the guidelines through first-half 2022.
TSA’s post-Colonial May 2021 directive required certain owner-operators take specific actions to enhance cybersecurity. In this directive, TSA requires, among other things, the owner-operators to report cybersecurity incidents to DHS. The directive also requires pipeline owner-operators to designate a cybersecurity coordinator and review current activities against TSA’s recommendations for pipeline cybersecurity to assess cyber risks, identify any gaps, develop remediation measures, and report the results to TSA and DHS.
A subsequent July 2021 cybersecurity directive established requirements for owner-operators to implement cybersecurity mitigation measures; develop a cybersecurity contingency and recovery plan; and undergo an annual cybersecurity architecture design review, among other things. The agency did, however, allow operators flexibility to submit alternative compliance options to TSA for consideration.
Increased federal role
According to GAO, the federal role in protecting the cybersecurity of critical infrastructure needs to be strengthened. In September 2020, GAO suggested that Congress consider legislation to designate a position in the White House to develop and execute a more comprehensive federal strategy for national cybersecurity and global cyberspace. In January 2021, federal law established the Office of the National Cyber Director within the Executive Office of the President. In April 2021, the President submitted Chris Inglis as his nominee for National Cyber Director. The Senate confirmed Inglis in June 2021 and the GAO tasked him with either updating the existing National Cyber Strategy and Implementation Plan or developing a new comprehensive strategy. GAO also called out the need to address cybersecurity workforce deficiencies both inside and outside the federal government.
In November 2021, Rep. Bobby L. Rush (D-Ill.) introduced HR 6084, the Energy Product Reliability Act. The bill would require the US Federal Energy Regulatory Commission to create an Energy Product Reliability Organization (EPRO) for the purpose of establishing and enforcing reliability standards.
Modelled after the North American Electric Reliability Corp., formed in the wake of 2003 and 2005 incidents exposing weaknesses in the power grid, EPRO would focus on threats—cyber or physical—to the reliable operation of the natural gas, crude oil, and refined products pipelines crossing the US. House Committee on Energy & Commerce hearings on the bill began in mid-January 2022.
Industry reaction
In August 2021, the American Fuel and Petrochemical Manufacturers, American Gas Association, Association of Oil Pipe Lines, American Petroleum Institute, American Public Gas Association, Interstate Natural Gas Association of America, and Gas Processors Association Midstream provided feedback on the July security directive, expressing concerns with its implementation and the process through which it was developed. These concerns centered on open communication, process transparency, and timely engagement, which the associations maintained were not fully realized during the directive’s development.
Most pointedly, they cited “several unanswered technical questions submitted by the associations…to which TSA guidance is critical for compliance” and the resulting “significant uncertainty” about what is required for compliance. They emphasized that TSA’s timeline to responding to questions should be consistent with the rapid deadlines established under the directive and asked TSA to apply learnings from the directive development process to improve the agency’s procedures for obtaining input on future pipeline security initiatives and “avoid recreating the implementation challenges and uncertainty” its members were experiencing.
As the directive was developed, industry conveyed highly probable operational safety and reliability concerns that could arise by imposing prescriptive cyber requirements and untenable timelines without specific understanding of a company’s existing cybersecurity protections and operations. TSA addressed some of the recommendations offered, but the associations still had “significant concerns.”
Included among these was that the broad scope and prescriptive nature of the directive would create potential conflicts with TSA pipeline security guidelines and with cybersecurity and safety regulations from other federal government entities. The associations also worried that the implementation schedule would create safety and reliability concerns and would hinder meaningful response to, and timely implementation of, any alternative compliance options put forward by members.
The associations urged TSA to reconsider its process for implementing pipeline security initiatives in the future to ensure better input on the compatibility of proposed security requirements with pipeline operational technology. “It is important TSA make timely updates to its pipeline security policies to keep up with evolving threats,” the associations said. “At the same time, it is equally important TSA’s process does not sacrifice input from the regulated industry for the sake of speed,” they continued, noting that both “TSA’s authorizing statute and the Administrative Procedures Act require the agency use formal notice-and-comment rulemaking as the primary vehicle for issuing new requirements.”
Finally, the associations reminded TSA that pipeline operators are best positioned to design mitigations to defend their systems against new threats and are unable to effectively prepare for threats about which they have not been briefed. The reminder came as part of voiced concerns that the speed with which the second directive had been promulgated was driven by new security threats which had not been shared with pipeline operators. It included the suggestion that TSA “work with the broader intelligence community to provide regularly scheduled briefings to pipeline industry experts to ensure operators are appropriately informed about the evolving threats to their systems.”
Following is the published list summarizing the associations’ requests:
- TSA and its technical experts should work closely and quickly with industry experts to ensure mutual understanding of how requirements in the directive could impact operational safety and reliability.
- TSA should release the technical FAQs immediately.
- TSA should provide clarity on anticipated criteria and timelines for review of alternative proposals, including addressing operator recourse if TSA disagrees with the alternative proposal and how TSA will address supply chain limitations.
- TSA should ensure operators are not penalized for awaiting TSA’s review of alternative proposals. TSA should provide more clarity on the directive’s scope so that operators can make more sound determinations of what is necessary to avoid disrupting operations or threatening pipeline safety.
- TSA should reconsider its process for implementing pipeline security initiatives in the future to ensure better input on the compatibility of proposed security requirements with pipeline operational technology.
- TSA and pertinent government intelligence community should brief all potentially affected pipelines on relevant cybersecurity threat intelligence as soon as possible.
Bibliography
US Department of Homeland Security, Testimony of Secretary Alejandro N. Mayorkas, Before the Committee on Homeland Security and Governmental Affairs, US Senate, “Threats to the Homeland: Evaluating the Landscape 20 Years After 9/11,” Sept. 21, 2021.
US Government Accountability Office, Statement of Leslie V. Gordon, Acting Director, Homeland Security and Justice, Before the Committee on Commerce, Science, and Transportation, US Senate, “Critical Infrastructure Protection: TSA is Taking Stepts to Address Some Pipeline Security Program Weaknesses,” July 27, 2021.
US Senators Rob Portman, James Lankford, M. Michael Rounds, Letter to The Honorable Joseph V. Cuffari, Inspector General, Department of Homeland Security, Office of the Inspector General, Oct. 28, 2021.
About the Author
Christopher E. Smith
Editor in Chief
Chris joined Oil & Gas Journal in 2005 as Pipeline Editor, having already worked for more than a decade in a variety of oil and gas industry analysis and reporting roles. He became editor-in-chief in 2019 and head of content in 2025.