Oil industry has new risk factor: terrorism
Although the oil and gas industry has always encountered elements of risk, traditional risk meant dry holes, foreign investments, unstable nation states, new ventures, and the occasional natural hazard. Man-made catastrophic events were not part of the risk profile and merited little attention beyond risks associated with insider sabotage or vandalism. The terrorist attacks of Sept. 11, 2001, in New York and Washington, DC, changed that environment dramatically and added sharp new focus to the industry’s approach to risk.
For reasons ranging from legal to fiduciary, quantifying and systematically analyzing this newly recognized risk have become increasingly important to an industry with physical assets around the world. Unfortunately, typical techniques and analytic approaches used by businesses to consider a proper business case for risk have proven difficult to apply in this new environment.
For operators, including terrorism risk seems daunting. The nature of the risk complicates its analysis. Companies may find it difficult to confront this new environment of adaptive and thinking adversaries and scarce relevant data and incorporate it into the context of risk management.
However, the industry can sharpen its approach to this important area by understanding definitions and quantitative techniques evolving in antiterrorism work. This article suggests ways to estimate and manage terrorism risk in oil and gas operations.
Lack of data
Quantification of this “new” type of risk has become increasingly important, but terrorism risk computations suffer from a lack of relevant statistical data. One cannot use classical probabilistic risk assessment tools such as those used in accident analyses where vast databases of component failures exist to enable rigorous models to be constructed.
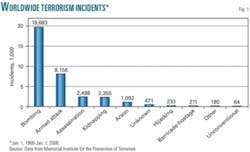
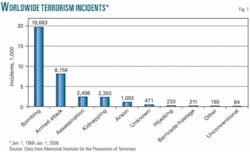
At first glance, it appears there is ample statistical data to employ classic probabilistic models. For example, Rand Corp. has more than 30,000 terrorist actions around the world in its database. The Memorial Institute for the Prevention of Terrorism includes over 34,000 terrorist actions committed since 1968 (Fig. 1).1 And the National Consortium for the Study of Terrorism and Responses to Terrorism includes over 80,000 terrorist actions since 1970.2 Even with what appears to be these impressive databases of terrorism events, Rand acknowledges that “the lack of historical data makes the use of experts the only way for modelers to determine the likelihood of new attacks.”3
There are a number of problems, pitfalls, and deficiencies associated with these databases. For example, a quick read of reported terrorist events exposes the difficulty of separating terrorist acts from criminal acts. Such fundamental problems of definition, the variety of terrorist organizations and motives, and the adaptability of terrorist methods and tactics make looking backward problematic in predicting future events. Data insufficiency poses problems for actuarial firms that provide risk models for the insurance underwriting industry, primarily because their contemporary best practices are based, in large part, on statistical approaches.4
Dating to 1977 is an exemplar discussion of some problems associated with risk related to such rare events within the energy industry as an attack on LNG facilities.5 In looking at terrorist attacks as both extreme and catastrophic events, Y.Y. Haimes says, “...no single probability density function…can be assigned to represent credible knowledge of the likelihood of such [terrorist] attack scenarios.”6
Definition of terms
Much confusion surrounding the topic of terrorism risk stems from the lack of consistent definitions of terms. The Security Analysis & Risk Management Association is attempting to standardize various terms in a lexicon that may or may not be adopted.7 Occasionally, the US Department of Homeland Security (DHS) publicizes glossaries, but these tend to be adapted to fit a particular topic and often are inconsistent with other DHS publications. Developing a working glossary is clearly a project in itself and is beyond the scope of this article; thus, the terms used here will rely on common usage or will be defined within the context of this discussion.
Consistent with traditional literature on risk, DHS identifies three components:
- Threat.
- Vulnerability.
- Consequence.
To capture the statistical nature of risk, the risk function classically is represented as the product of the probability and results of a particular outcome. However, as noted by many authors, using probabilities based on prior history for dealing with adversaries, e.g., Al Qaeda, Hezbollah, or even the Earth Liberation Front, is limited by their ability to be adaptive and creative in devising new attacks. The adaptability of terrorists in varying tactics, target sets, diversions, and simultaneity compound the problem. Further, statistical probability implies that all possible outcomes are known. Such is certainly not the case with terrorist attacks.
With these limitations in mind, DHS created a surrogate for probability. This surrogate comprises threat and vulnerability. Along with consequence, this becomes a type of conditional risk that is a function of many other variables, only a few of which can be addressed here.
The US Department of Defense (DOD) identifies threat as an adversary having intent, capability, or opportunity to cause loss or damage.7 However, recent work by J.F. Williams indicates that, with respect to radical Islamic terrorism, there is a third component to threat spaceauthority.8 This additional threat element has both an internal and external function.
Internal authority is necessary in order for a terrorist organization to sustain its activity on a global level, to maintain membership and support, and to provide religious cover to terror agents whose actions are viewed as sacramental duties rather than acts of violence.
External authority, better understood as legitimacy, is necessary to attract recruits and supporters, to convince the group’s audience of the legitimacy and acceptability of target and attack modes, and to justify the magnitude of the attack. In fact, Williams’ concept can probably be expanded to nearly any terrorist organization because, save for the lone wolf, someone must decide and commit to carrying out the attack in some form of cultural threat space.
National security considerations are not conducive to information-sharing with the oil and gas (or any private) industry. Only recently has DHS been able to participate with fusion centers in various states, but most personnel manning these sites deal in classified intelligence information, which is fed as appropriate to local law enforcement and national authorities. Gleaning the intent, capability, and authority of any given threat stream from such rare and necessarily nonspecific unclassified reports can be nearly impossible. However, some sources of unclassified information open source intelligencecan help operators develop profiles of possible threats in their areas of operation.
If intent, capability, and authority are known, the precise means, often referred to as attack mode, may represent a critical independent variable in an overall estimation of threat. For instance, Al Qaeda professes that it would use weapons of mass destruction (WMD) against the US. While having the intent and religious authority to do so, however, at present it appears that it does not have the capability. Conversely, the use of improvised explosive devices (IEDs) of varying sizes is a well-used tactic, but their effect is less than that of WMD.
Even if information were available to estimate the likelihood of a given type of terrorist attack such as an IED or vehicle-vessel borne IEDs (VBIED), questions remain as to selection of the most cost-effective array of countermeasures. This is because details necessary to fully determine the likely delivery “character” of an attack are seldom discussed. For example, what is the blast area of a given IED charge in the target area? Or what is the likely delivery mode of a VBIED: a lone panel truck? a convoy with sniper preparatory fire to pin down facility security personnel?
In many instances, such information is available, or could be, but doesn’t seem to be considered newsworthy. As a result, even facility owners determined to take action are left to wonder which specific countermeasures to choose.
Although there is no assurance that available attack characteristics will define a future attack, there is merit in using them when considering countermeasures. As a general proposition, terrorists tend to develop an approach that works and then stick to it; in fact, they train on it. Constructing IEDs is often tricky work, and those who can often build and provide a steady supply for delivery; their techniques are taught in training camps.
Delivery tactics, on the other hand, are more often adaptive and tend to remain unchanged until countermeasures used against them force it. Following the evolution of both bomb-making and delivery techniques can provide useful tools when considering cost-effective countermeasures.
Vulnerabilities of any given physical or cyber asset are often uncovered during safety and security analyses. Making assessment an even greater challenge, recent work regarding hurricane damage to offshore platforms suggests that vulnerability to damage is asset-specific as well as attack specific.9 10 Quantifying vulnerability is tedious work and remains something of an art form.11 12 13 Methodologies such as DOD’s criticality, accessibility, recuperability, vulnerability, effect, and recognizability (CARVER) have been found to be of limited value when comparing vulnerabilities across a spectrum of assets in various geographies.14
In business, consequences of a terrorist attack are usually measured in dollars and casualties, which can be converted to dollars. Other aspects such as capacity to perform mission or psychological impacts cannot easily be quantified, though these can and do impact continuity of operations, and therefore profitability. How companies approach potential losses is reasonably well established if the loss is part of an understood threat. Hurricanes do not learn from previous storms, nor do they target specific assets to maximize destruction. Unfortunately, the same cannot be said of terrorists, the one class of threat agent that learns and adapts to developments.
Security as a cost
In some ways security is similar to other costs of doing business such as sales, administration, maintenance, and environmental and regulatory compliance. It competes against other expenditures, and tradeoffs are made in the corporate interest. But in other ways, security is very different. Maintenance problems do not learn, nor are they deterred. Regulations generally do not focus solely on single facilities within a complex so only maximum disruption is prevented.
Security costs, like the others mentioned, should be considered in a cost-benefit analysis and factored in like any other sunken cost as a normal cost of doing business. Performing such an analysis of terrorist attacks, however, is problematic because at whatever scale (unit, site, region, state, country, worldwide), assets prioritization is required. This implies that quantification of riskand, as importantly, quantification of countermeasures and response capabilitiesis necessary. In other words, risk management should be quantified as much as possible if dependable estimates of cost-benefit ratios and security investment prioritizations are to be made.
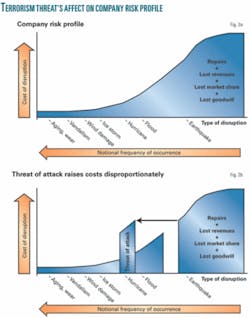
Insurance underwriters strongly support the Terrorist Risk Insurance Act of 2002 (reauthorized in 2005 and 2007) because it limits their exposure to claims in the event of a terrorist attack having significant losses.15 The Mortgage Bankers Association notes: “As real estate capital markets continue to weather industry turmoil, extending terrorism risk insurance will resolve an important area of capital market uncertainly [sic]the long-term availability of terrorism insurance.”16 Self-insured oil and gas operators may run significant risks if terrorist attacks are not included in their risk profile. Fig. 2a shows a notional risk profile for a company regarding typical interruption events, and Fig. 2b illustrates how a risk profile can change when an imminent threat is identified.
Because quantification of terrorism risk is not especially amenable to conventional probabilistic tools, prioritization of security investments and insurance coverage are also uncertain. However, some inroads to this challenge are being made.
Risk computation
Within the terrorism risk communitya discipline essentially born on 9/11there is debate about what are the proper mathematical operations that relate to the variables of threat, vulnerability, and consequence.
One can argue that if any of the values that make up terrorism risk is zero, the risk is either nonexistent or of little concern. That is, if a particular asset is perfectly invulnerable, regardless of how valuable it may be, how many people want to destroy it, or how many threats against it have been documented, its risk is of no real concern. Implicitly, this statement converts to a simple formula of risk being the product of threat, vulnerability, and consequence.
While it is improbable that any of the threat, vulnerability, or consequence variables truly would be zero, some attacks can realistically be taken out of consideration either because their consequences are so low as to be insignificant or because the attack is of such enormous magnitude (i.e., a nuclear attack) as to make preparations essentially impossible or irrelevant, at least within the realm of the private sector.
It is unlikely that many operators have built and maintain databases that have even a small fraction of all the data required for making such a calculation even for a single asset, much less for a site, region, or global portfolio of assets.
Some challenges
The 9/11 Commission Report and other writings have documented a number of intelligence community failures to “connect the dots” prior to the 9/11 attacks.17 18 While federal intelligence groups seek to improve their methods in this regard, the missions of the various agencies and their previously embedded culture of secrecy suggest it may be some time before such improvements are realized.19
While there is a need for secrecy of classified information, a robust open source intelligence process may well provide sufficient information to perform risk assessments. Intelligence gathering has long been performed by the private sector, and carefully focusing some of that capability towards potential terrorist threats within areas of concern may serve operators well. However threat information may remain the most uncertain of the data needed for quantitative terrorist risk assessments, in large part because threat information, unlike vulnerability and consequence information, is solidly within the hands of the adversary.20
The problem of uncertainty is not only manifested in threat. Typically, there also are more than one asset type in any given geographic area. “Critical infrastructure is often geographically concentrated, so it may be distinctly vulnerable to events like natural disasters, epidemics, and certain kinds of terrorist attacks,” said P. Parfomak in a report of the Congressional Research Service. “Additionally, disruption of concentrated infrastructure could have greatly disproportionate effects, with costs potentially running into billions of dollars and spreading far beyond the immediate area of disturbance.”21
Risks to all assets of one type within an area are not identical. For instance, assuming that threat and vulnerability values were equal, the risk from attacks to petrochemical plants along the Houston Ship Channel could differ greatly because the potential consequence to human health will vary by individual specific asset. A truly comprehensive risk assessment would sum the risk of all possible combinations of threat, vulnerability, consequence, and attack modeclearly an overwhelming task.
Other considerations include both spatial and functional interdependencies. Spatial interdependency is the collocation of two infrastructures, a common example being telecommunication lines “hosted” by vehicular bridges. There is no relation between the two other than their location at the same place on the ground. Should an attack occur that involves, say, explosives, both infrastructures could be affected, regardless of the intent of the perpetrator. Functional interdependencies are too often illustrated by cascading failures such as happened in the 2003 Northeast blackout.
Another major parameter baffling risk analysts is how to measure risk reduction from implementing various types of protective or countermeasures or increasing response capabilities. With the possible exception of nuclear material facilities, workers in the field have been largely unable to quantify the value of countermeasures or capabilities across the risk spectrum and have therefore been unable to measure risk reductionthe defining and singularly important task in the overall risk management. This problem further plagues our ability to justify investments in a conventional cost-benefit sense.
Ranking assets
From an operator’s standpoint, the issue of terrorism risk can be addressed using an approach as described above tuned to specific circumstances. The accuracy and precision of “risk numbers” must be considered as highly uncertain but perhaps no more so than new exploration ventures.
Like other investments, the risk prioritization approach will provide a relative ranking. Getting started is usually the biggest hurdle because it seems overwhelming. However, close collaboration within a company’s security, finance, human resources and other departments and among companies within a particular region will better prepare everyone for potential losses.
With no statistically valid basis for estimating a probability of attack, we are unable to defend a classical cost-benefit approach.
However, some method must be used to rank or prioritize assets, if only locally, to ensure prudent security investments. Consider the following along with standard continuity of operations planning:
- What attack types concern me most?
- Who are the potential perpetrators, and what is driving them? It may help to adopt an “observed or worst-case terrorist tactic” approach, with different tactics for each entity (asset-site-region-operator-country-portfolio).
Close cooperation between, and acceptance by, each faction of the company is necessary to maximize risk management, including threat identification and vulnerability and consequence mitigation.
While quantification of risk can be difficult, the discipline of working through it for the company’s most important assets is essential to long-term security.
Risk is ubiquitous. For this industry, avoiding it is not a luxury. Although risk assessment as a tool of understanding and managing risk through remediation or loss-transference is as much an art as it is a science, operators should not ignore the science dimension. Present private sector risk models assessing terrorism threats are incomplete, undisciplined, and problematic. By embracing a more robust approach to risk through the aggressive management of risk’s components, a company may begin to understand, respond to, and manage its own threat and risk profile.
Until then, companies in an industry that terrorist groups have identified as a high-value target will maintain inadequate security programs where the absence of an attack is mistaken for an effective antiterrorism security program.
References
- Memorial Institute for the Prevention of Terrorism (www.tkb.org/Home.jsp).
- National Consortium for the Study of Terrorism and Responses to Terrorism (START) (209.232.239.37/gtd1/charts/weapon_type_pie.gif), 2007.
- Willis, H.H., Morral, A.R., Kelley, T.K., and Medby, J.J., “Estimating Terrorism Risk,” Rand Center for Terrorism Risk Management Policy, The Rand Corp. Monograph Series MG-388, 2005.
- Grossi, P., and Kunreuther, H. (editors), “Catastrophe modeling: A new approach to managing risk,” Springer Science, New York, 2005.
- Fairley, W.B., “Evaluating the ‘small’ probability of a catastrophic accident from the marine transportation of liquefied natural gas,” in Statistics and Public Policy, Fairley, W.B., and Mosteller, F., (editors), Addison-Wesley, Reading, Mass., 1977, pp. 331-353.
- Haimes, Y. Y., “Risk Modeling, Assessment, and Management” (Second ed.), Wiley-Interscience, Hoboken, NJ, 2004.
- Security Analysis and Risk Management Association (sarma-wiki.org/index.php?title=Category:Definitions),2007.
- Williams, J.F., “Al-Qaida Strategic Threats to the International Energy Infrastructure: Authority as an Integral Component of Threat Assessment,” Proc. of Carlton UniversityOttawa Center for Infrastructure Protection, 2007.
- Kaiser, M.J., Pulsipher, A.G., Singhal, A., Foster, T., and Vojjala, R., “Catastrophic Event Modeling1; How coverage has evolved for offshore storm risks,” (OGJ, Dec. 3, 2007, p. 36).
- Kaiser, M.J., Pulsipher, A.G., Singhal, A., Foster, T., and Vojjala, R, “Catastrophic Event Modeling2; Industry exposure and value at risk to storms in the Gulf of Mexico,” (OGJ, Dec. 10, 2007, p. 36).
- Garcia, M.L., “Vulnerability Assessment of Physical Protection Systems,” Elsevier Butterworth-Heinemann, Burlington, Mass., 2006.
- Woo, G., “Quantitative Terrorist Risk Assessment,” Risk Management Solutions, (www.rms.com/NewsPress/ Quantitative_Terrorism_Risk_Assessment.pdf), 2007.
- Ezell, B.C., “Infrastructure Vulnerability Assessment Model (I-VAM),” Risk Analysis, Vol. 27, No. 3, 2007.
- US Department of Defense special operations forces acronym (CARVER) used throughout the targeting and mission planning cycle to assess mission validity and requirements, (usmilitary.about.com/od/glossarytermsc/g/carver.htm), 2007.
- Daily News and Information for the Mortgage Loan Originator (originatortimes.com/content/templates/standard.aspx?articleid=2697&zoneid=6), 2007.
- Ferraiolo, T., “Terrorism Risk and Insurance,” The Gosline Insurance Group (www.homelandsecuritynys.org/news/2007/terrorismrisk.pdf), 2006.
- The 9/11 Commission Report (www.gpoaccess.gov/911/), 2004.
- Wright, L., “The Looming TowerAl-Qaeda and the Road to 9/11,” Vintage Books, New York, 2006.
- Clark, R.M., “Intelligence AnalysisA Target-Centric Approach,” (2nd ed.), CQ Press, 2007.
- Williams, J.F., “The Nature of the Terrorist Threat “Proc. of Conference Board of CanadaTargeting the World’s Transportation Systems: 2007.
- Parfomak, P., “Vulnerability of Concentrated Critical Infrastructure: Background and Policy Options,” Congressional Research Service, Order Code RL33206, 2005.
The authors
David M. Weinberg ([email protected]) is president and CEO of Practical Risk LLC, a terrorism risk analysis consulting firm. His work is an outgrowth of his previous risk analyses at the Department of Homeland Security’s Office of Infrastructure Protection, where he developed methods for allocating Homeland Security grant funds. Weinberg began work in the petroleum industry with Cities Service Oil Co. in 1970. After receiving his PhD from Texas A&M University in 1977, he spent more than 17 years with Conoco in upstream and research and development positions followed by 12 years with the Idaho National Laboratory. Weinberg is a member of American Association of Petroleum Geologists, Society of Exploration Geophysicists, Society of Petroleum Engineers, and the Society for Risk Analysis.
Glenn H. Coplon ([email protected]) is an independent operations research analyst in Falls Church, Va., doing contract work in both threat and risk analysis for the Department of Homeland Security. He previously was a longtime employee in the Department of Energy’s Office of Energy Emergencies. Coplon holds a BS (1956) in mathematics from Virginia Tech and has done graduate work in economics at both Virginia Tech and George Mason University.
Jack Williams, JD, CIRA, CDBV ([email protected]) is a professor of law at Georgia State University College of Law in Atlanta and the scholar in residence at the American Bankruptcy Institute in Alexandria, Va., where he is researching risk in the energy industry, among other topics. He serves as a consultant to the federal government and the private sector on threat analysis, risk assessment, infrastructure protection, counterterrorism, and Jihadist theory and tactics. He has addressed the American Petroleum Institute’s annual meeting, security professionals within API, the National Petrochemical & Refiners Association, the American Chemistry Council, and American Society for Information Science. Williams is a member of the American Bar Association, the Coast Guard Auxiliary, the Federalist Society, and the American Statistical Association and is a fellow in the American College of Bankruptcy. Williams also is a director in BDO Consulting, where he serves as a financial advisor, forensic accountant, and financial fraud detection expert. Williams has authored four books and over 100 articles and papers.