SPECIAL REPORT: Workshops identify threats to process control systems
Recent industry workshops have identified the issues of cyber and physical security risks to process control systems (PCS). There are many cyber and physical security risks to the oil and gas infrastructure, and it is generally recognized that even a small process disruption could produce many serious consequences that result in safety, environmental, and economic impacts.
This article focuses on the characterization of the cyber risks associated with PCS and describes components of risk that can assist in understanding an organization’s security posture and implementing effective mitigations and protection.
The increased connectivity between PCS and business networks and the widespread migration to off-the-shelf hardware and software has increased the exposure to outside threats and broadened known vulnerabilities. This has led to the increased awareness of PCS security and protection.
To address PCS risks, the Institute for Information Infrastructure Protection (I3P) has funded a multi-year research program to improve PCS security in the oil and gas industry (see www.thei3p.org/research/scada for more information on this project). Under this program, I3P hosted two PCS security workshops-which included oil and gas asset owners, PCS and security vendors, PCS researchers, and government officials-to explore the underlying security issues and discuss mitigation strategies.
These events occurred in June 2005 in Houston, and in June 2006 in La Jolla, Calif. Research and analysis performed by I3P were presented and interaction facilitated with industry through discussions about PCS security concerns, cyber risks for automation systems, emerging threats, and new technologies.
This article summarizes major concerns voiced at the I3P workshops and discusses a broader understanding of PCS security risks and solutions based on research and professional experience in this area. Risk is characterized in terms of threats, vulnerabilities, and consequences. Protective measures and business impacts are also addressed.
Industry can use this characterization as a starting point to assess major areas of concern in their own operations, possible consequences of an attack, and return on investment (ROI) of implementing defenses. Understanding and characterizing this risk will enable the development of strategies for preventing, detecting, mitigating, and recovering from cyber-security incidents with focused and defined objectives.
Input from industry collectively provides a strong basis for both decision-making and improvements with realizable, specific outcomes.
Critical industry observations
Input for the risk-characterization process was obtained primarily from industry stakeholders through workshops and interaction, gap analyses performed under I3P activities, and related PCS research. The first I3P workshop gathered a wealth of industry perspective. The second I3P workshop validated the approaches towards technology, application, and emerging ideas on secure operations.
Industry concerns
Members of industry segments voiced their concerns at panels during the workshops. These concerns can be grouped into different technical domains:
- Wireless security. Security is lacking in wireless connectivity and remote access to enterprise systems. Wireless security must be addressed as part of the enterprise architecture. There is the 802.11 protocol in production fields, but a more secure, capable solution is needed across the infrastructure and in remote areas.
- Intrusion detection. Basic intrusion detection is often lacking in an architecture, which includes monitoring, event correlation, and alarms. This security control is essential to detecting and preventing attacks.
- Understanding and implementation of security. A comprehensive view and implementation of security is often missing; a piece-meal approach to security is common. Currently, there is sporadic or little implementation of controls across the system. One layer, such as a firewall or physical security, is not enough to prevent an attack. A layered, comprehensive approach is necessary.
- Legacy systems. Many legacy systems that have interoperability issues or hardware and software constraints are still in use. These systems have minimal security controls and are difficult to patch or upgrade, resulting in vulnerabilities without clear mitigation strategies and a weakening of the overall architecture. Addressing these legacy systems and developing a solution for protection is needed.
- Standards. No widely accepted standard for security implementation in control systems exists. Non-standard security controls are therefore applied over a variety of domains, including business systems, PCS, and physical (site) security. A comprehensive, layered approach is needed with guidelines for an enterprise approach to security.
- Training and awareness. Training and awareness of security configurations is necessary to prevent the incorrect implementation of security controls, such as firewalls.
- Design. Basic security, such as authentication, access control, and encryption, is not designed into many control systems. The need for add-on security can create implementation difficulties. Upgrades and added functionality to aging control systems can result in the introduction of commercial technology that can add new vulnerabilities. Considering security at the beginning and throughout the control system lifecycle is critical for continual, secure operations.
- Network structure. Many PCS are connected to business networks within the enterprise. Without separation or controls placed between the architectures, attackers have a potentially exploitable access path to gain control over operations. There is greater risk, therefore, to core functions and operations.
- Policies and plans. In addition to guidelines and standards in the approach to and implementation of security, enterprise level security policies and plans are needed to ensure security is implemented at the necessary levels of protection. The organizational divide that exists in many organizations between IT and PCS groups can thwart effective policy and procedure implementation.
- Incident handling. Part of robust security includes data backups as well as the preservation and analysis of forensic data. Developing a plan for maintaining this data is important to understand and mitigate future attacks.
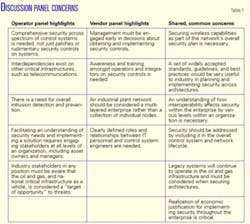
Interestingly, concerns from industry members often reflect the body of industry they represent. For example, panel members at the first I3P workshop were divided into operator and vendor groups and it was interesting to note the differences and commonalities in their responses.
This emphasizes the need for increased communication across the stakeholder community in a multi-front approach to security.
Table 1 outlines highlights from both panel discussions.
Risk characterization
Characterizing risk for control systems is different than identifying risks purely associated with finances, safety, or IT. It is a blend of all those risks with their effect on operations and the ability to perform the critical functions necessary to continuously provide a product or service, e.g., refine crude or transport refined products in a pipeline.
In this case, risk is characterized in terms of threat, vulnerabilities, consequences, and impact on business (Fig. 1). Organizations that identify and fully define these components find them to be the first step in securing operations.
Threat assessment
Creating an understanding of threat and an awareness that critical infrastructure can be an attractive target is generally the first step in protecting critical operations.
The goal of a threat assessment is to determine the likelihood of an attack against a given target. Threats to control systems in the oil and gas sectors can be derived based on access, intent, and system vulnerabilities. A typical threat assessment includes:
- Identification of known and potential adversaries.
- Analysis of each adversary’s motivations, goals, and capabilities.
- Assessment of the threat posed by each adversary to critical system assets.
When applied to a specific control system or set of systems, a threat assessment is normally quite detailed and specific.
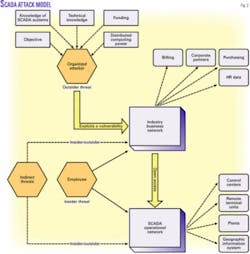
Threats can be characterized by both their level of access, motivations, and their capabilities. A threat implies that an individual or group has the ability and access to carry out a process that creates damage to, or exploits, a system for a specific gain. The result can have physical, economic, environmental, and human consequences.
Threats to control systems can come from both insiders and outsiders and can vary in capability. Capability is a function of resources such as time, money, computing power, technical knowledge, and intelligence resources.
Threats and their capabilities are often divided into several specific categories such as nation-state, international terrorists, domestic terrorists, or hackers. Although individual hackers may have malicious intent and technical knowledge, organized cyber-terrorist groups often possess the resources necessary to carry out an effective, distributed attack that produces severe consequences.
Characteristics that can affect a threat’s success in an attack include funding, goal intensity, stealth capability, access, cyber skills, implementation time, and cyber-organization size.
A targeted organization has no capability of controlling these characteristics, with the exception of access. An organization’s physical and cyber defenses are therefore critical.
Access to information about control systems, including design details, weaknesses, and protective measures, are often available on the Internet. Likewise, industry and corporate-specific data can easily be gathered from basic Web investigative techniques.
In combination, this information can be very useful to a threat planning a coordinated attack and, because this information is readily available, increased protections implemented on networks become the primary line of defense. This defense can ensure operations are not disrupted or compromised.
Because these threats exist today and organized cyber-terrorists continue to gain resources and capabilities, industry must address this as a present and future issue.
Fig. 2 illustrates an attack and lists its potential effects, which include downtime, exploited information for financial gain, strained strategic partnerships, safety hazards, and damage to infrastructure.
For example, once a threat accesses a control system, often through a business system, it is possible for the attacker to assume privileges as though he or she were a trusted insider. This control could potentially result in access of control systems that manage the lifeblood of an organization.
In some instances, threats are not targeted toward an organization or one specific goal. For example, widespread worms and viruses can create an overall slowdown and damage, but are generally not used to produce a specific effect on one organization. Likewise, untrained employees or accidents by employees can pose a threat to the organization by inadvertently creating security holes.
These indirect threats should be considered when addressing security in control system operations in addition to threats with targeted, malicious intent.
Quantification of threat and understanding how that threat relates to their own assets can help industry members take the initial steps in building a secure operating environment.
Vulnerability analysis
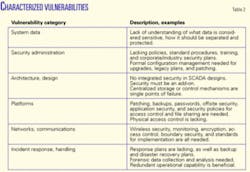
A vulnerability is a weakness that exists in a system, network, application, or process that can be exploited by a threat to create an adverse effect. Examples of vulnerabilities can include open ports, unpatched software, dated virus protection, or exploitable system services.
Vulnerabilities can be identified through a frequent assessment process or review, and can be reduced using different mechanisms. These mechanisms can include patches, access controls, network protocols, monitoring, and physical controls.
Vulnerabilities discussed at the I3P workshops include descriptions of broad categories as well as specific examples. Table 2 outlines these categories.
Understanding vulnerabilities and how they exist and evolve within an architecture is necessary when selecting and applying security protective measures. As a whole, the oil and gas industry is becoming more aware of vulnerabilities and how they arise, and are now looking for ways to mitigate them.
Vulnerabilities can be identified and reduced, but continual maintenance is required to safeguard elements of the architecture and operations as a whole. Vulnerability assessments are particularly useful in determining the current state and robustness of an organization’s architecture. Identified technical vulnerabilities, however, are often not meaningful to management when making choices to invest in security.
Vulnerabilities must be viewed as only one part of a whole when considering risk to control systems and the organization. Different members of the organization, and of the industry, may have different priorities. Awareness and communication is required to create a comprehensive security plan that prioritizes assets and provides guidelines for applying protective measures.
Consequences
A consequence is the resulting loss, damage, or impact resulting from a threat successfully exploiting a vulnerability. Consequences can include access and alteration of data, disruption of service, destruction of the system, and severe environmental and public health results of an attack.
Based on the threats and vulnerabilities discussed, consequences to control systems could potentially be severe due to physical and operational effects. Some consequences can have serious effects on business operations, to the industry as a whole, and to the national critical infrastructure.
Understanding consequences of a successful attack can help an asset owner identify areas of the architecture that need higher levels of protection and prioritize the deployment of protection mechanisms. The consequences of an attack have direct effects on the organization or industry as a whole.
These effects include:
- Physical effects that encompass direct consequences of control system misoperations. The most devastating potential effects include personal injury or loss of life. Other effects include the loss of property (including data) or damage to the environment.
- Economic effects are secondary results of physical impacts ensuing from an attack. Physical impacts could result in repercussions to system operations, which in turn inflict a greater economic loss on a plant or company. On a larger scale, these effects could negatively affect the local, regional, national, or possibly global economy.
- Social impacts or public image. A side effect that is often overlooked is the consequence of losing national or public confidence in an organization or industry. It is, however, a very real objective and one that can be accomplished via a cyber attack.
- Impact on national critical infrastructure. Industry sectors are a part of the whole national infrastructure. Loss or adjustment of capacity and delayed purchasing and transportation create secondary effects on the national infrastructure. Likewise, attacks on other industries in the national infrastructure can affect the oil and gas sectors. An example reiterated at the workshops is the reliance on the telecommunications industry.
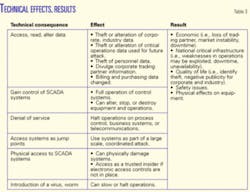
Table 3 breaks down example consequences, effects, and overall impacts. If a threat exists that can exploit an existing vulnerability, any number of these consequences can occur.
Although Table 3 does not contain every potential consequence, it is important to understand how a threat with an opportunity can create negative consequences. Understanding components such as the network, platforms, system data, and operational policies can help in creating a layered approach to protecting the infrastructure.
Business effects, ROI
Determining the consequences of an attack based on an analysis of threats and vulnerabilities is useful to understanding exactly what to protect on control system networks. Workshop participants recognized, however, that implementation of security controls is often an expensive task. There must be a visible ROI to justify the expense of deploying additional security technology such as hardware, software, or physical controls.
It is probably most analogous to insurance, although the financial benefit to stopping attacks on a daily basis is rarely quantifiable. An asset owner must therefore consider the potential cost of not employing these controls. Downtime and the halted production or transport of oil and gas can be directly translated to profit losses.
To some extent, safety can also be quantified in the number and cost of accidents and injury. The social impacts, however, such as quality of life and the effect on critical infrastructure at a national level are not easily measured.
For example, an organization must consider how customers and the market will view it if it suffers a publicized attack. Likewise, if a corporation’s unsecured control system network is used as an entry point or active node in a coordinated attack on the national infrastructure, it can have devastating business consequences in addition to the infrastructure damage.
This scenario is not unlike that of airline companies who have suffered a business loss or faced near bankruptcy due to eroding public confidence caused by a hijacking or safety-related crash. The price of inaction can be far costlier than implementation of security to the architecture.
Protective measures
Defenses against cyber attacks are most effective when applied in multiple layers of security through what is sometimes referred to as a “defense-in-depth strategy.” Often specific controls are implemented that only partially address protection, such as firewalls, but protection and defense must be viewed as a comprehensive task.
Vulnerabilities can be mitigated and threats deterred by using a layered approach that groups areas of concern. These logical areas that require defense can include data, applications, platforms, networks and communications systems, and perimeter systems. Breaking apart these layers, organizations can map their processes and determine exactly what needs to be protected and how to defend it.
These defenses and protective measures could include:
- Access control.
- Authentication.
- Applied operating system and platform security.
- Data separation.
- Functional separation.
- Network design.
- Encryption.
- Patches, upgrades.
- Monitoring and event correlation.
- Backups and disaster recovery plans.
- Alerting mechanisms to discover coordinated attacks.
- Redundancy in connectivity.
- Firewalls and perimeter security.
- Secure remote access.
- Trusted computing platforms.
- Accepted measures for risk characterization elements.
In combination, and with an operational focus, these measures can provide the best defense against attack. Understanding the critical functions and data types in the system and applying appropriate security controls to segregated architectural enclaves is essential for a comprehensive defense.
In addition to the use of technology in security controls, a comprehensive and well-understood security plan is required. This plan should address physical, personnel, and information security, and should mandate as many controls as required to secure operations. In this plan, it is also necessary to address the technology lifecycle.
As operations and equipment evolve, security must be fluid and provide the functionality required by the current situation. In addition to lifecycle planning, legacy systems must be assessed and a methodology developed for either upgrading or replacing these systems.
In developing a plan and applying controls, forging a common understanding among different industry and organizational groups is essential. This means creating awareness and discussion among all stakeholders to include asset owners, vendors, IT personnel, operators, and management. Involving and obtaining feedback from members across the enterprise can result in a security plan that is most effective while ensuring continuity of operations.
Further work
A growing understanding of threat, vulnerabilities, and consequences in the oil and gas industry can lead to effective implementation of security technology and methodologies. These implementations will produce inherently secure operations, ensuring reliability, continuity, safety, and important steps toward a secure national infrastructure.
Implementing robust security measures across facets of an organization takes communication across all levels of the organization, established objectives, and a committed effort to ongoing maintenance. Because all threats cannot be eliminated and vulnerabilities continue to evolve, a layered approach to security and a comprehensive implementation plan is necessary.
Continued collaboration between industry and researchers will yield new technologies and approaches that mitigate risk and foster a secure operating environment. A third I3P workshop is planned for February 2007 that will include demonstrations of common vulnerabilities and associated mitigation tools and techniques.
This I3P effort is coordinating with other PCS security research programs and industries to develop ideas for comprehensive security. These activities will yield an accurate picture of the most important issues.
Acknowledgments
The authors thank the June 2005 I3P workshop participants for the open discussion of security issues, which formed the basis of this article. The authors also recognize Martin Stoddard of CVO Electrical Systems, LLC, Erin Pratt of Pacific Northwest National Laboratory, and Yacov Haimes, Matthew Henry, Joost Santos, and Kenneth Crowther of the University of Virginia.
Bibliography
“Generic Threat Profiles,” Report SAND2005-5411, Sandia National Laboratories, Albuquerque.
“A Reference Model for Control and Automation Systems in Electric Power,” Report SAND2005-1000C, Sandia National Laboratories, Albuquerque.
“A Scalable Approach for Critical Infrastructure Security” Report SAND2002-0877, Sandia National Laboratories, Albuquerque.
“Common Vulnerabilities in Critical Infrastructure Control Systems” SAND2003-1772C, Sandia National Laboratories, Albuquerque.
Kilman, D., and Stamp, J., “Framework for SCADA Security Policy,” Report SAND2005-1002C, Sandia National Laboratories, Albuquerque.
“I3P National Cyber Infrastructure Bulletin,” Vol. 1, No.1, Sandia National Laboratories, Albuquerque.
“I3P SCADA Security Workshop Raw Data Report,” Sandia National Laboratories, Albuquerque.
“Industry Security Needs/Concerns,” Powerpoint presentation.
“Penetration Testing of Industrial Control Systems,” SAND2005-2846P, Sandia National Laboratories, Albuquerque.
“Security Guidelines for the Petroleum Industry,” American Petroleum Institute, April 2005, http://api-ec.api.org/filelibrary/Security.pdf.
“Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries,” 2nd Edition, American Petroleum Institute and National Petrochemical & Refiners Association, October 2004, http://api-ec.api.org/filelibrary/SVA_E2.pdf.
Stamp, J., et al., “Sustainable Security for Infrastructure SCADA,” Report SAND2003-4670C, Sandia National Laboratories, Albuquerque.
The authors
Annie McIntyre is a senior member of the technical staff at Sandia National Laboratories, Albuquerque. In the Networked Systems Survivability organization, her primary areas of research include threats, vulnerabilities, and protection of critical infrastructure under the I3P program and leading security metrics efforts under the National SCADA Test Bed. Previous to this, McIntyre worked extensively in the defense sector on information warfare and survivability, serving as IO Laboratory Chief and Information Warfare Lead for Future Combat Systems Assessments at the Army Research Laboratory. She previously served as New Mexico Regional Manager for Concurrent Technologies Corp. and performed systems analysis and engineering under the Human Genome Project. She holds a BS from New Mexico Tech, an MS from Troy State University, and is a member of AAPG.
Jason Stamp is a principal member of the technical staff at Sandia National Laboratories, where he has more than 7 years’ experience in the field of information systems and national security. His research areas include the development of improved tools for information security and the integration of network technology into security architectures for infrastructure, homeland security, and the military. Stamp holds a BS (1995) in electrical engineering from the Rose-Hulman Institute of Technology, Terre Haute, Ind., and a PhD (1998) in electrical engineering from Clemson University. Jason is a member of the Power Engineering Society of IEEE.
Ben Cook is a principal member of the technical staff at Sandia National Laboratories. He currently leads research efforts on robust critical infrastructure systems and supports the management of Sandia’s process control research and development. Cook is the technical project leader for the I3P’s process control security research program, and Sandia’s project lead on the DHS LOGIIC project. His technical background is in modeling and simulation with an emphasis on large-scale natural and engineered systems. Cook holds a ScD in information technology from the Massachusetts Institute of Technology.
Andrew Lanzone is a senior member of the technical staff at Sandia National Laboratories. He has several years experience in both cryptographic research and applied cryptography with an emphasis on algorithm development and software programming. Lanzone spent several years designing and analyzing cryptographic protocols and digital security systems. He holds a BS in electrical engineering from Grove City College, Pa., and a Masters of computer science and engineering from the University of Michigan.